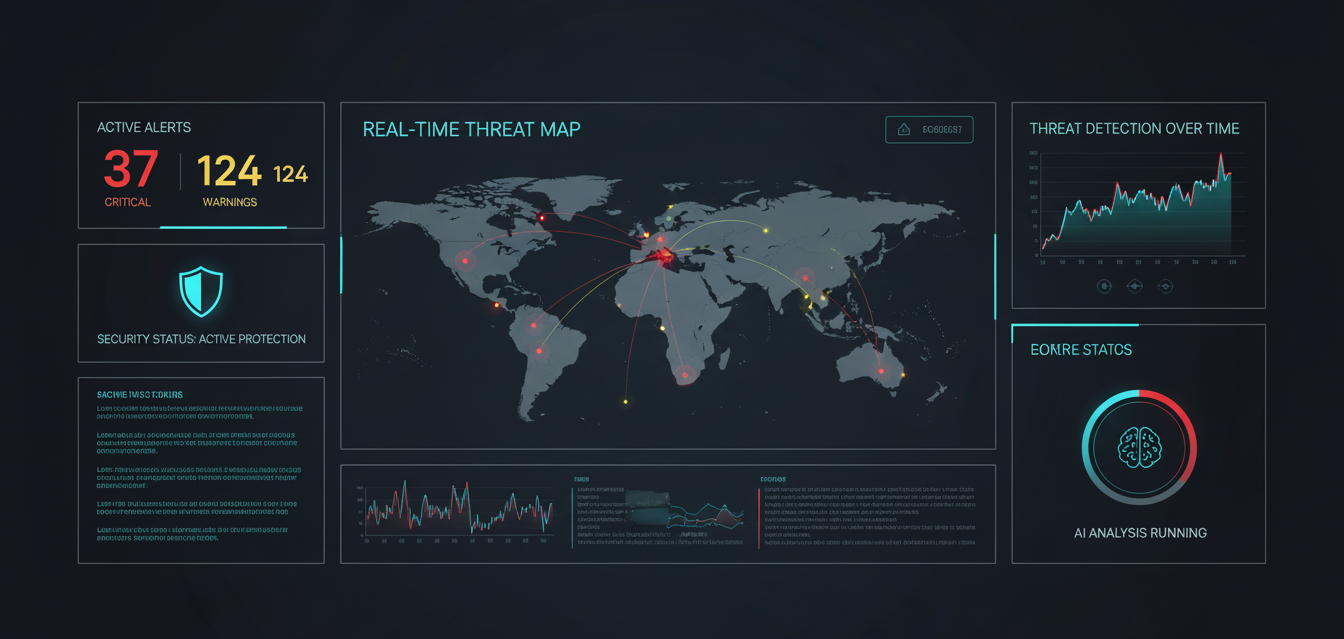
Make Security YourTransformation Advantage
Transform cybersecurity from a cost center to a competitive advantage with AI-powered threat detection, advanced security operations, and proactive risk management that protects your digital assets 24/7.
End-to-End Cybersecurity Services
Comprehensive security solutions designed to protect, detect, and respond to modern cyber threats with AI-powered intelligence and 24/7 monitoring.

Audits & VAPT
Comprehensive security assessments and vulnerability assessments & penetration testing to identify and remediate security gaps before attackers can exploit them.
- Compliance audits (ISO 27001, GDPR, RBI, and other regulatory standards)
- Information security audits and policy reviews
- Vulnerability scanning (network, application, and cloud)
- Penetration testing (external, internal, and web applications)

SOC Design & Operations
24/7 security operations center with advanced threat detection, SIEM implementation, and automated response capabilities to protect your digital assets around the clock.
- SIEM implementation
- SOAR automation
- Threat intelligence
- Incident response
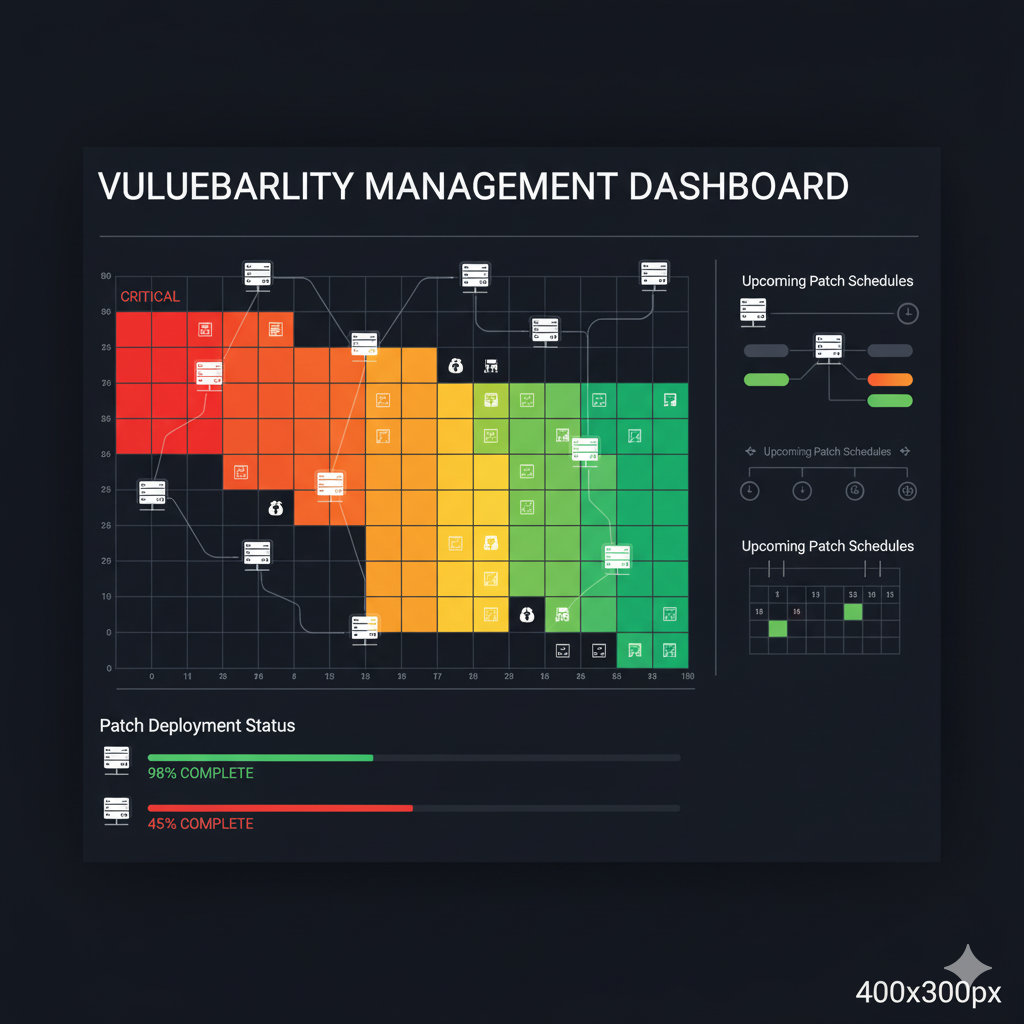
Vulnerability & Patch Management
Proactive vulnerability identification and automated patch deployment across your infrastructure to stay ahead of emerging threats and maintain security posture.
- Vulnerability scanning
- Patch automation
- Risk prioritization
- Compliance reporting
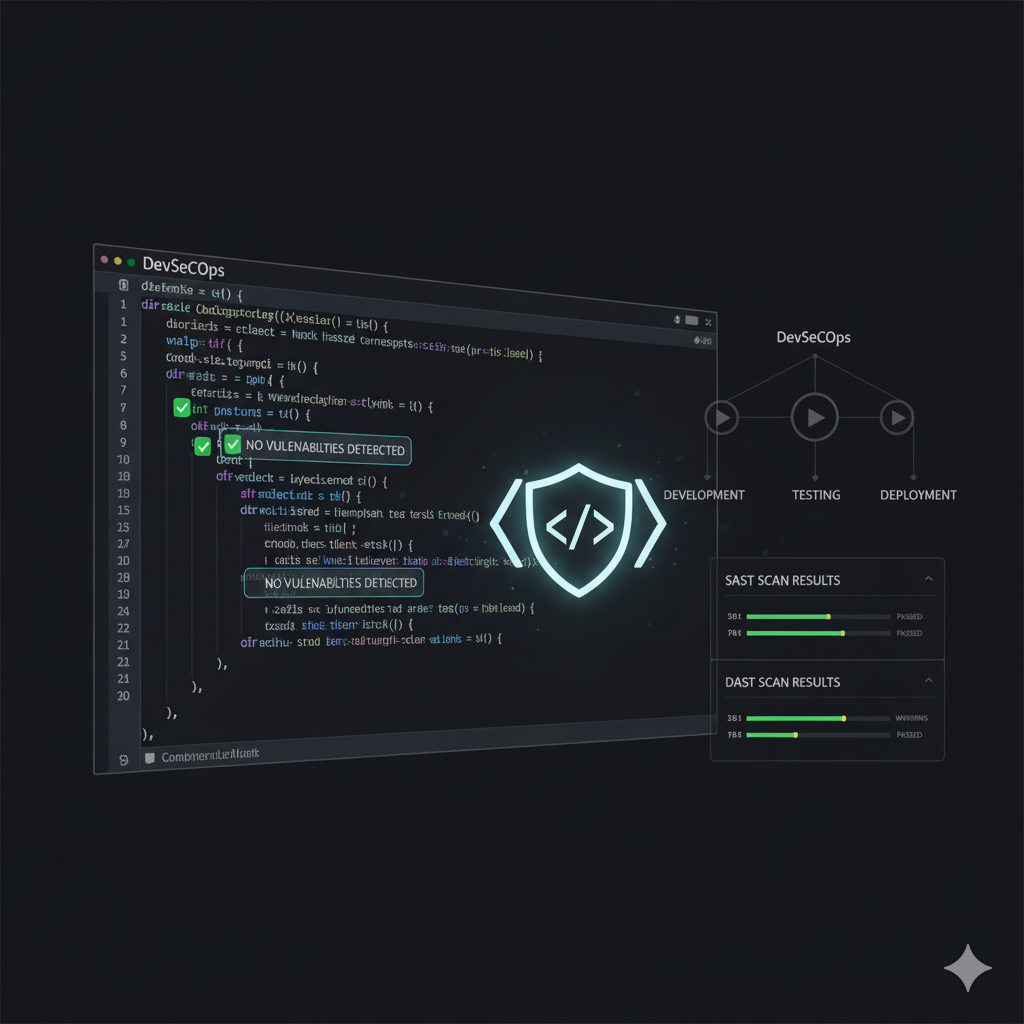
Application Security
Secure software development lifecycle with comprehensive security testing, code review, and DevSecOps integration to build security into every application layer.
- SAST/DAST scanning
- Code review
- Security testing
- DevSecOps integration
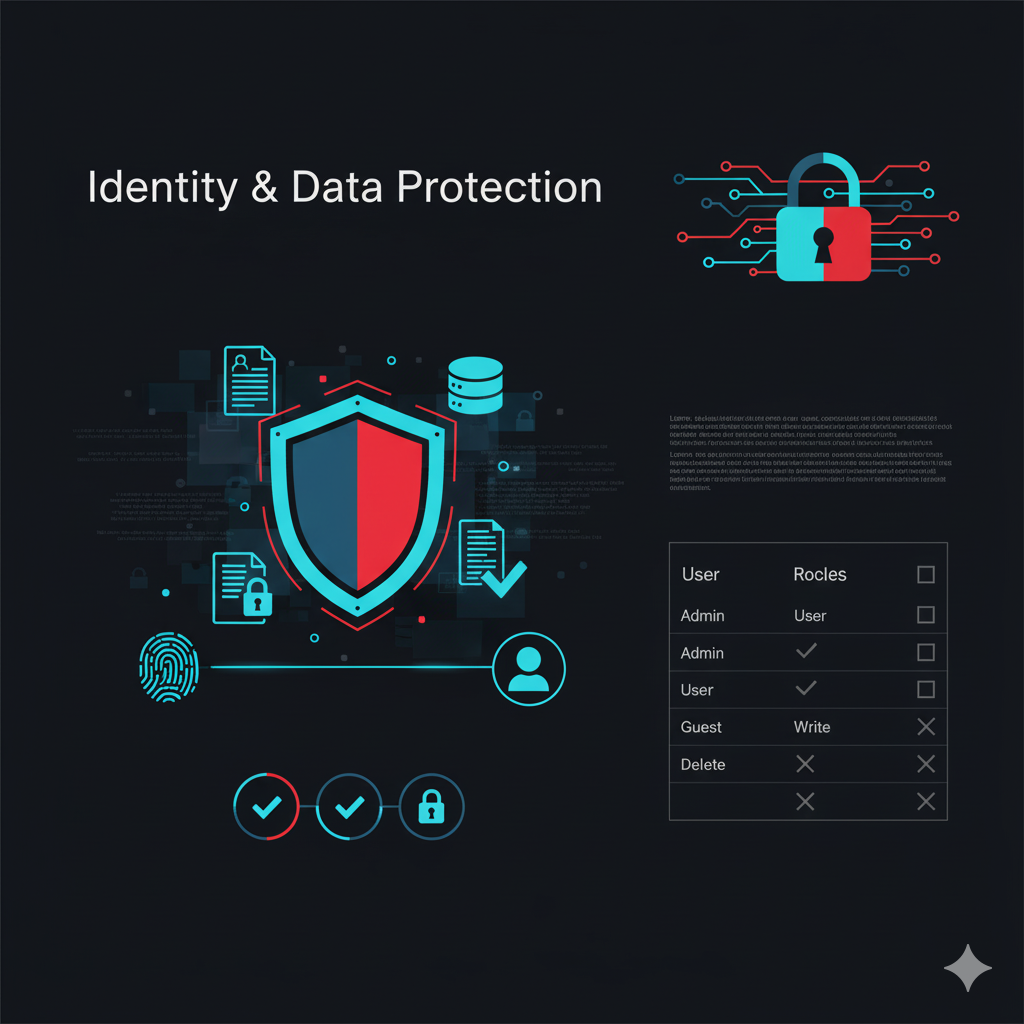
Identity & Data Protection
Robust identity management and data protection solutions with EDR, DLP, and IAM to safeguard your critical assets and ensure regulatory compliance.
- IAM solutions
- DLP implementation
- EDR deployment
- Access control

Brand & Surface Monitoring
Comprehensive monitoring of your digital footprint with deep/dark web monitoring, phishing detection, and proactive threat intelligence for brand protection.
- Deep/dark web monitoring
- Phishing detection
- Brand protection
- Surface monitoring
Accelerate Security withArtificial Intelligence
Leverage cutting-edge AI and machine learning to transform security operations, automate threat response, and achieve unprecedented protection with intelligent analytics that work 24/7 to safeguard your infrastructure.
AI Threat Intelligence
Leverage AI and machine learning to accelerate threat detection and response with intelligent security analytics

AI-Powered Threat Detection
Machine learning algorithms that analyze patterns and detect anomalies in real-time, identifying sophisticated threats before they can cause damage. Our AI models continuously learn from global threat intelligence.
Intelligent Security Analytics
Advanced analytics that process billions of security events to identify critical incidents, prioritize alerts, and provide actionable insights for rapid response and remediation.
Automated Response Orchestration
AI-driven SOAR platform that automates incident response workflows, reduces mean time to respond (MTTR), and eliminates manual processes for faster threat neutralization.
Predictive Security Posture
Leverage AI to forecast potential security vulnerabilities and predict attack vectors based on historical data, threat intelligence, and environmental factors for proactive defense.
AI-Powered Security Performance
0%
Threat Detection Accuracy
0%
Faster Response Time
24/7
Continuous Monitoring
AI Security Services in Partnership withBosch AIShield
Enhancing AI security through our strategic partnership with Bosch AIShield, offering comprehensive solutions to protect your AI systems against emerging threats with enterprise-grade security technology.
AISpectra | Model Scanner
Automates model and notebook discovery, performing in-depth vulnerability assessments to secure the AI supply chain.
AISpectra | ML Red Teaming
Conducts automated red teaming to expose vulnerabilities like adversarial attacks, model theft, and data poisoning.
Guardian | ML Firewall
Provides real-time protection for machine learning applications by detecting and mitigating adversarial threats.
Our Strategic Technology Partners










































Transforming Businesses throughStrategic Security
Vulnerability Assessment for India’s Leading Oil & Gas Company
CONTEXT
Client wanted to implement a process of continuous Vulnerability Management existing network, databases, devices, end point systems. The client wanted to integrated the identified vulnerabilities into a live dashboard view of their SOC Setup for a quicker response to the identified threats.
SOLUTION
Rigved got involved in reviewing the network architecture and strategically placing the Vulnerability Management Process for identifying the vulnerabilities and related exploits in their critical infrastructure and also integrating the same with existing SOC for better mitigation.
RESULT
Client has a better picture of their IT infrastructure from the purview of IT security and because of continuous Vulnerability Management, Client Infrastructure is more secured and less prone to cyber attacks.

Why Choose Our Cybersecurity Solutions?
Advanced AI-powered security capabilities that protect your business while enabling digital transformation.
Zero Trust Security
Implement zero trust architecture to eliminate implicit trust and continuously verify access.
AI Threat Intelligence
Advanced AI-powered threat intelligence and analysis to stay ahead of emerging cyber threats.
Automated Response
Automated incident response and remediation to minimize breach impact and recovery time.
Compliance Assurance
Maintain compliance with industry standards and regulatory requirements across all operations.
Ready to Strengthen Your Security Posture?
Partner with Rigved to implement AI-powered cybersecurity solutions, achieve 99.9% threat detection, and protect your business with enterprise-grade security that works 24/7.
Free comprehensive security assessment • No commitment required • Confidential evaluation • AI-powered insights