We’ll Work with You to Develop the Capabilities You Need to Make Secure Enterprise Transformations
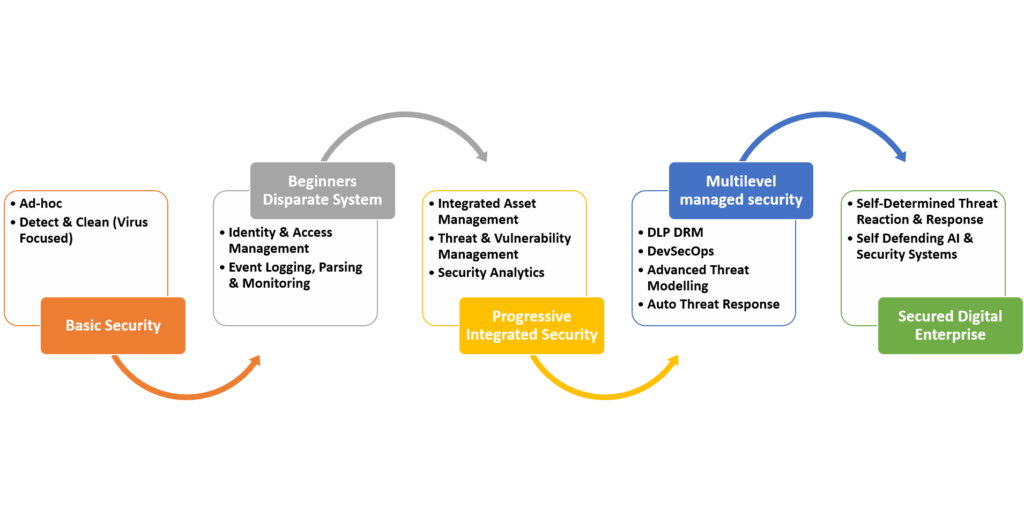
Among the technological foundations driving digital transformations, Security emerges as the most intricate yet indispensable element for success, often operating in the shadows. Data reveals a startling reality: cybercrime is advancing nearly twice as fast as digital transformation itself. Without robust security measures, the prospects of digital transformations remain bleak.
Traditionally, cybersecurity incidents such as hacking, intellectual property theft, financial fraud, and ransomware attacks remained largely concealed. However, recent incidents have shattered this perception, with malevolent actors not only obtaining their objectives but also garnering significant negative publicity. Cybersecurity breaches no longer solely entail financial ramifications; they tarnish a company’s brand image and erode the trust of stakeholders.
Beyond the high-profile breaches, data underscores a concerning truth: nearly 70% of breaches go undetected and consequently unreported. This alarming statistic stems from the fact that over 60% of companies lack comprehensive threat assessments, rendering them ill-prepared for such eventualities. Unfortunately, by the time they realize the severity of the situation, it’s often too late to respond effectively.
Furthermore, the repercussions extend far beyond the affected company’s bottom line. The colossal costs and damages inflicted upon customers and, by extension, entire nations due to the loss of intellectual property and sensitive information underscore the urgent need for stringent security regulations on a global scale.
Rigved as an organisation is highly focused on providing below cyber security services to clients;
Audits and Assessments
- Identify Critical Assets
- Recognize Potential Threats
- Profile and Map Risks to Standards
- Conduct Vulnerability Assessments
- Perform Network & Application Security Testing
- Review Configurations, including Mobile Applications
Security Operations Solution
- Evaluating SOC performance through comprehensive reviews
- Crafting strategic plans and roadmaps
- Executing implementation and operational setup
- Designing and implementing Threat Intelligence strategies
- Deploying Security Incident & Event Management (SIEM) systems
- Implementing Security Orchestration, Automation & Response (SOAR) solutions
Threat Intelligence
- Threat Model Analysis
- IOCs Aggregation
- Website, Vendor, and Blog Monitoring
- Brand Activity Surveillance
- Deep/Dark Web Monitoring
- IRC and Cybercrime Forum Tracking
- Company Reputation and VIP Account Monitoring
- Phishing Attempt Detection
- Emerging Threat Management
Vulnerability Management
- Conducting Vulnerability Assessment and Penetration Testing (VAPT)
- Managing Infrastructure Vulnerabilities
- Performing Web Application VAPT (Static and Dynamic Analysis)
- Ensuring Compliance through Scanning
- Assuring Firewall Integrity
- Managing Patches and Vulnerabilities
- Reviewing Code to Identify Security Flaws and Vulnerabilities
Security Operations
- Identity and Access Management (IdAM) and Authentication
- Data Protection including DLP and DRM, Endpoint Security, Antivirus, and EDR
- Integrating security, orchestration, and configuration management solutions
- Developing Security Content
- Implementing SOAR (Security Orchestration Automation & Response)
We provide cyber security services not only to protect Software as a Service (SaaS) solutions but also to safeguard shared-service organizations. Rigved is able to bring a much deeper understanding of critical infrastructure, computer security, and security policy to your organization. Let us step in as your cyber security resource or to augment existing IT capabilities not only for approaching your environment from an impartial perspective but also for resolving your most complex security issues. Rigved Technologies will help you to enhance your existing security controls and improve capabilities with our actionable cyber threat data.
